Day 07: Trust Me
C'mon bro, trust me! Just trust me!! Trust me bro!!!
Challenge Info
- Name: Trust Me
- Category: Miscellaneous
- Points: 10
- Author: John Hammond (@_JohnHammond)
Challenge Description
C’mon bro, trust me! Just trust me!! Trust me bro!!!
The
TrustMe.exeprogram on this Windows desktop “doesn’t trust me?”It says it will give me the flag, but only if I “have the permissions of Trusted Installer”…?
Challenge File: N/A
Solution (Static)
In this challenge, we connect to a virtual machine that contains the “TrustMe.exe” executable. As a teammate of mine blooded this using a utility that allows you to run a binary as TrustedInstaller, I decided to pull the executable from the VM to solve statically and by mucking with the code flow.
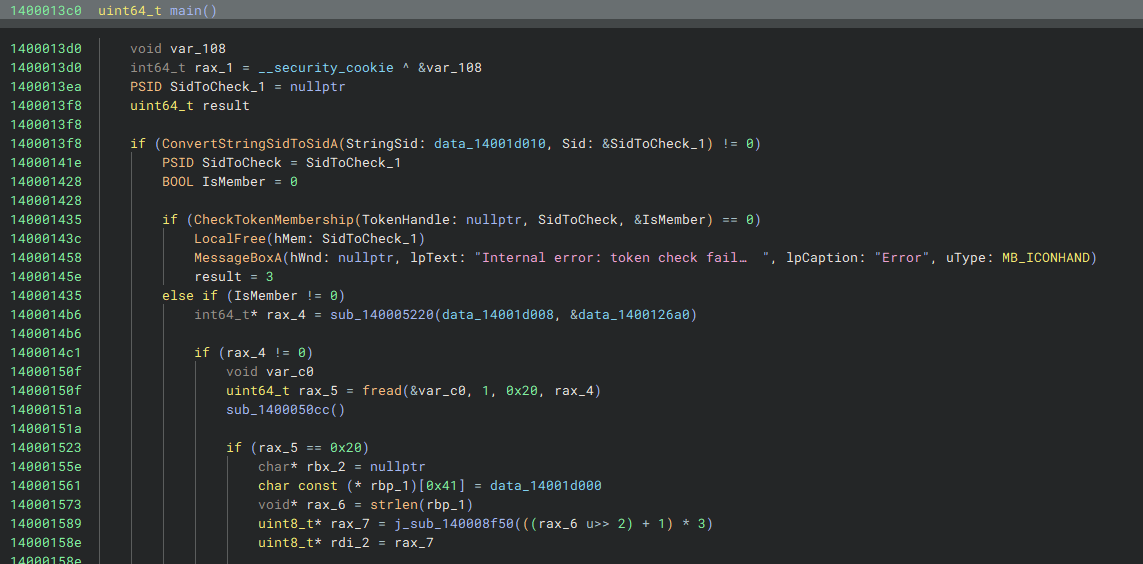
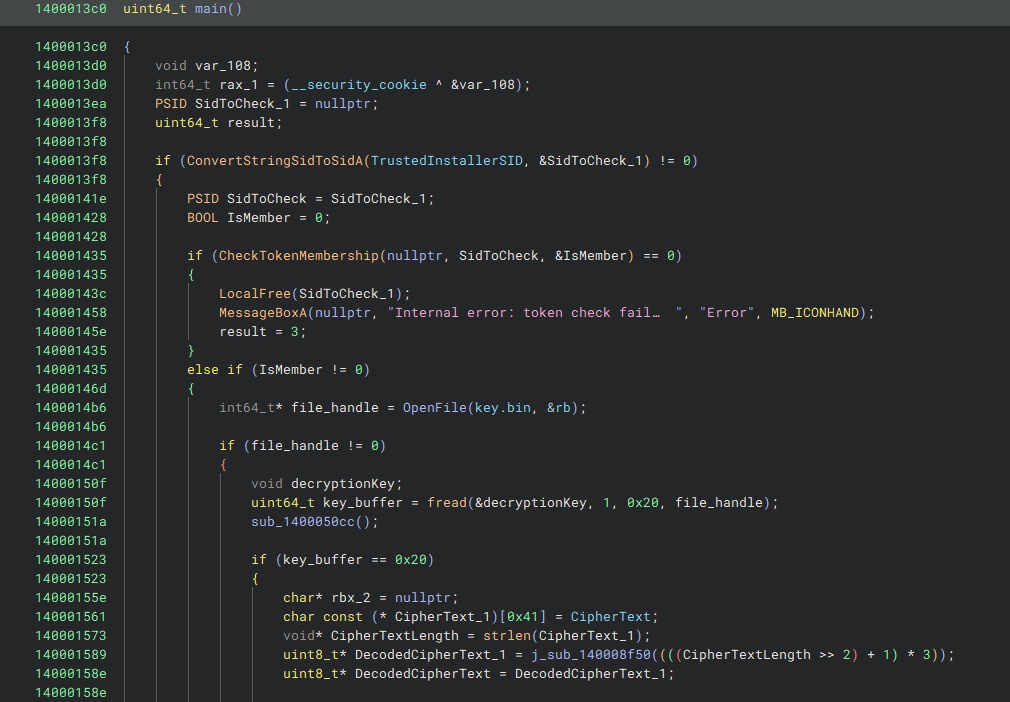
First, we’ll solve this statically - opening TrustMe.exe in Binary Ninja and navigating to main(), we can see that a string representation of a SID is being converted to a SID structure to be used with CheckTokenMembership(), which checks whether or not the specified SID is enabled in the user’s access token.
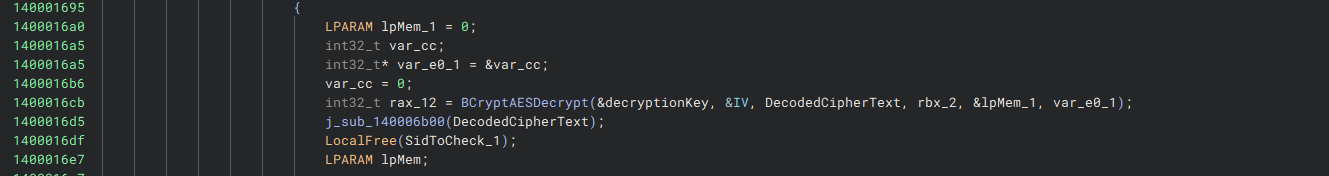
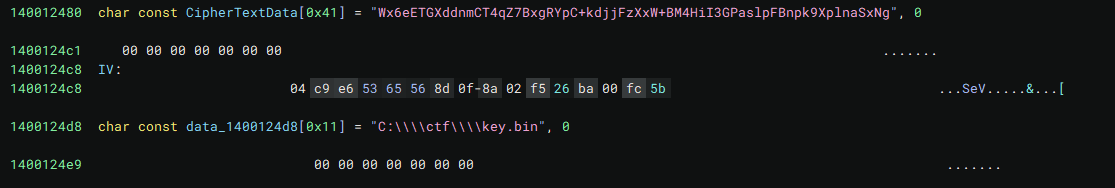
Cleaning up the function and variable names a bit, we can see that the binary is checking for the TrustedInstaller SID. On a success, the binary opens a handle to the C:\CTF\key.bin file in rb mode, and reads its contents to a buffer. Afterwards, it takes a hardcoded IV and Base64-encoded Ciphertext, Base64-decodes the ciphertext, and uses BCrypt to decrypt the decoded ciphertext bytes with the IV and the key read from C:\CTF\key.bin.
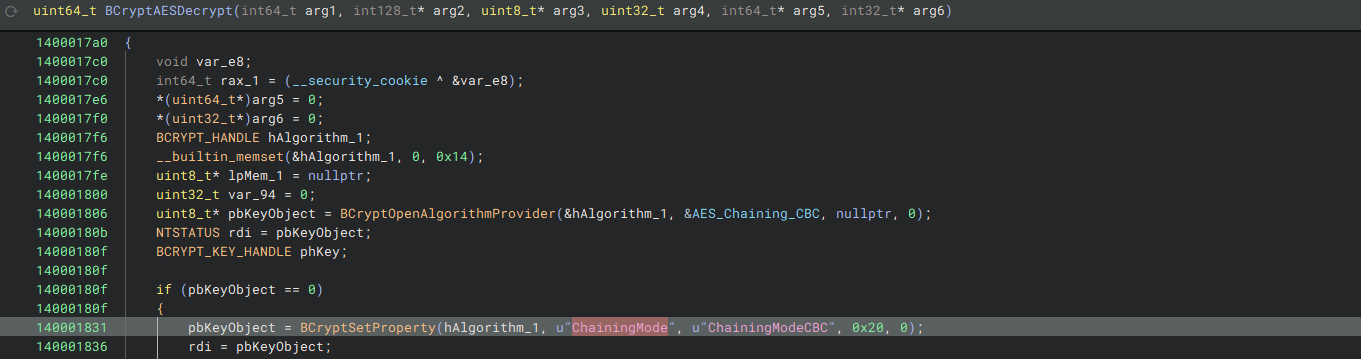
Taking a look at the underlying BCrypt implementation, we can see that the ciphertext is being decrypted with AES-256-CBC, which is great! We can make a refinery pipeline to decrypt this quite easily.
The IV has a quite identifiable pattern to regex for, and the ciphertext is the largest Base64 string in the binary, which makes for a quite reliable pipeline.
First, we’ll use ef to emit the data from TrustMe.exe. Then, we use push [| emit key.bin | pop key ] to push the original data from TrustMe.exe out of scope while we emit the data from key.bin (so we aren’t overwriting the output from ef), and pop that data to a variable called key.
Then, we push again, this time using regex (rex) to carve the IV from the binary data, and storing that as a variable called IV.
Finally, we use carve -ds b64 to carve and decode the largest Base64 blob (the ciphertext), and decrypt it with AES-256-CBC using the stored IV and decryption key.
All together:
1
2
3
4
➜ ef TrustMe.exe [| push [| emit key.bin | pop key ] \
| push [| rex -u '.{3}SeV.{5}\&.{3}\[' | pop IV ] | carve -ds b64 \
| aes --mode cbc --iv var:IV var:key ]]
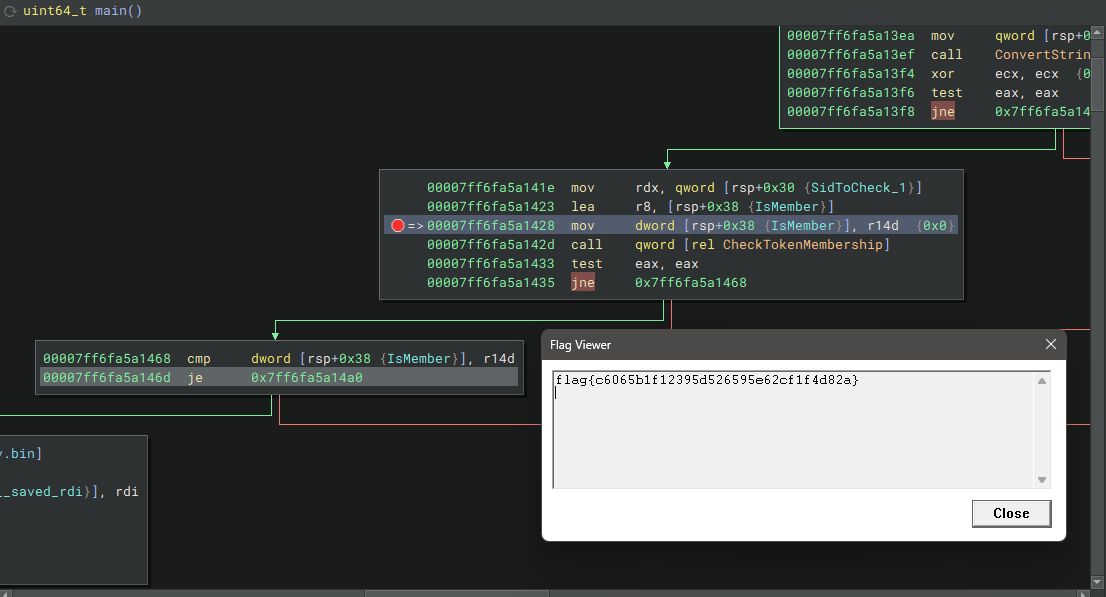
flag{c6065b1f12395d526595e62cf1f4d82a}
Solution (Dynamic)
The solution is much more straightforward and simple if we want to solve this dynamically - simply place key.bin in C:\CTF, place a BP anywhere before the cmp comparing the result from the call to CheckTokenMembership, and flip the logic from jne to a je - the program will return the decrypted flag once you continue from your BP 😄
Flag
1
flag{c6065b1f12395d526595e62cf1f4d82a}